CGNAT Explained: Why You Cannot Port Forward with Your ISP
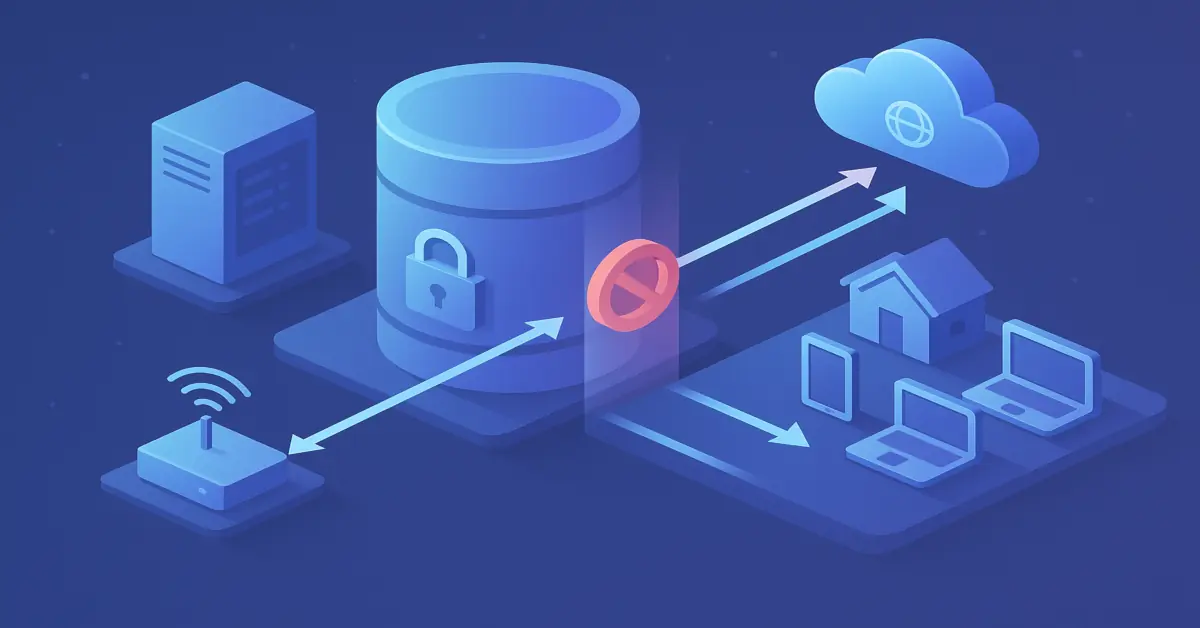
Port forwarding that used to “just work” on a home router often fails today, even when you swear you opened the right port and pointed it at the right device. The missing piece is usually upstream of your network: your provider put you behind carrier-grade NAT, so the internet can’t initiate a connection back to you.
If you run a game server, self-host media, or need remote desktop into your PC, CGNAT turns successes into timeouts. The request never reaches your WAN interface, so no router rule can help. That’s not a bug in your setup; it’s an architectural choice your ISP made to stretch scarce IPv4 addresses across many customers.
The good news: you’ve got several workable paths around it. Some are one-phone-call simple, others involve tunnels or IPv6. We’ll map the landscape, show how to confirm you’re behind CGNAT, and help you pick the least painful fix for your use case.
How CGNAT Works
CGNAT (carrier-grade network address translation) lets an ISP share one public IPv4 address among dozens or hundreds of subscribers. Instead of assigning a unique public address to your router, the ISP gives your router a private address in an internal provider network and performs a second layer of NAT in their infrastructure. This is commonly called NAT444: a private LAN behind your router, an ISP-side private space, and finally the public internet.
Key Address Ranges You’ll See
Residential routers typically use RFC 1918 private ranges like 192.168.0.0/16, 10.0.0.0/8, or 172.16.0.0/12 on the LAN. ISPs operating CGNAT often hand out addresses from RFC 6598’s dedicated shared space 100.64.0.0/10 on the WAN of your router or on their intermediate edge. If your router’s WAN IP is itself private or in 100.64.0.0/10, you’re not directly on the public internet.
What This Means for Inbound Traffic
NAT makes outbound connections easy: the translator creates ephemeral mappings as your devices talk out. But for inbound connections, a translator needs an explicit static mapping from a public port to a specific internal host and port. Your home router can create such a mapping (port forwarding) only for the NAT it controls. The ISP’s upstream translator won’t know about your rule, so unsolicited traffic destined to the shared public IP never gets mapped down to you.
Why Port Forwarding Fails Under CGNAT
When you “open a port” on your router, you tell the first NAT to expect inbound packets on its public side and forward them inside. Under CGNAT there is no true public side on your router; there’s just another private hop toward the ISP’s NAT. The upstream translator never receives a configuration telling it to forward to your line. Even if your router supports UPnP or NAT-PMP and an app opens a port successfully there, it can’t punch a pinhole in the ISP’s translator. Peer-to-peer apps sometimes do NAT traversal via UDP hole punching (STUN) or relays (TURN), but symmetric NATs—common in CGNAT deployments—break hole punching, and relays add latency and cost.
How to Confirm You’re Behind CGNAT
First, compare your router’s WAN IP to a public IP check. If the two don’t match, the ISP is translating again. If your WAN IP sits in 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16, or 100.64.0.0/10, you’re definitely not uniquely reachable. Second, run a traceroute to any site and look at the first one or two hops; private ranges there also indicate upstream NAT. Third, many consoles and games report “Strict” or “Type 3” NAT under CGNAT. Finally, external port scans will show your supposed open port as filtered or closed because packets don’t reach your line.
Options to Reach Services Behind CGNAT
There isn’t a single silver bullet because your constraints vary: budget, control, protocols, and latency needs. Choose the least complex option that meets your requirements.
Ask Your ISP for a Public IPv4
This is the cleanest fix when available. Some providers offer a public dynamic IPv4 on request; others sell a static IPv4 add-on. Once assigned, your router sits on a real public address and your existing port forwards start working. Verify you’re no longer in 100.64.0.0/10 or RFC 1918 on the WAN, and disable any temporary tunnels to avoid hairpin surprises. Downsides: monthly fees, potential waiting lists, and in some regions it’s simply not offered.
Use an Inbound-Friendly VPN or Your Own VPS Tunnel
Two patterns are common. First, a commercial VPN that supports inbound port forwarding can terminate a public port on their server and forward traffic over an encrypted tunnel to your device. Latency rises by the detour to the VPN point of presence, and some providers limit which ports or protocols you can forward. Second, rent a low-cost VPS with a public IPv4, run WireGuard or OpenVPN between your site and the VPS, and publish services on the VPS using reverse proxies (for HTTP/HTTPS) or port redirection for arbitrary TCP/UDP. This gives you stable addressing and full control, at the cost of configuring and maintaining a small internet-facing host.
Leverage IPv6 Where Both Sides Support It
IPv6 eliminates the need for NAT for inbound reachability. If your provider delegates you a global IPv6 prefix, every host can have a globally routable address. To expose a service, allow it in your firewall and advertise its AAAA record in DNS. Clients on IPv6 will connect directly without port forwarding. Be aware: many mobile networks and some cafés still do IPv4-only, so dual-stack (serve both A and AAAA) or provide a fallback via a tunnel or proxy. Also confirm your IPv6 prefix stability and router firewall defaults, which often block unsolicited inbound by design.
Use Application-Level Relays and Tunnels
For browser-based and HTTP workloads, an application relay often suffices. Reverse-proxy tunnels can accept HTTPS on a cloud endpoint and stream it into your LAN over an outbound tunnel initiated by you, which bypasses CGNAT entirely. SSH reverse tunnels can expose a port on a remote server you control and forward it back home. Peer-to-peer collaboration tools and game platforms sometimes provide their own relaying backplanes, trading some latency and bandwidth overhead for connectivity.
Security and Operational Notes
Getting back on the public internet doesn’t mean opening the floodgates. NAT was never a security feature; your real protection is the stateful firewall on your router or host. When you publish a service, reduce its attack surface: prefer TLS, set strong authentication, keep software updated, and restrict source IPs when possible. If you use a VPS, treat it like production: patch promptly, back up configs, and monitor logs.
NAT Types, STUN/TURN, and P2P Apps
Multiplayer games and voice/video apps attempt NAT traversal with STUN to discover reflexive addresses and with UDP hole punching to establish peer flows. CGNAT devices often behave as symmetric NATs, assigning unique external ports per destination, which breaks hole punching. In that case the app must fall back to a TURN relay, adding a middle hop and latency. That’s why you see “Strict NAT” and higher ping until you move to a public IP, an inbound-capable VPN, or IPv6.
Dynamic DNS, DNS Records, and rDNS
Dynamic DNS is helpful when your public address changes: a client resolves a stable hostname and still reaches you. Dynamic DNS alone does not bypass CGNAT; it just points to wherever your public address is. It becomes useful once you have either a real public IPv4 or a public endpoint like a VPS or relay to publish records for. For mail servers, reverse DNS (rDNS) on the public IP must match your hostname to avoid spam rejection, which is usually only configurable by the IP’s owner (your ISP or VPS provider). To verify that mapping, run an rDNS Check on the public IP to confirm the PTR record matches your hostname (FCrDNS) and spot misconfigurations.
Testing and Verifying Your Setup
After any change, test from outside your network. For IPv4, check whether the world sees your new public address and scan the intended port from an external vantage point. For IPv6, verify your hosts receive global addresses, confirm your firewall rules permit inbound flows, and test from an IPv6-capable client. Log both the service and the router/firewall to trace failed attempts, and consider rate limits to blunt basic scans.
Decision Guide: Which Path Should You Take?
If you host latency-sensitive game servers for friends, a public IPv4 from the ISP is usually the simplest and lowest-latency route. If you only need web apps or SSH, an HTTP reverse-proxy tunnel or an SSH reverse tunnel is fast to deploy and easy to secure. If you care about open protocols and want complete control, a small VPS plus WireGuard gives you a reusable “public edge” for multiple services. And if your audience is IPv6-capable, enabling IPv6 and publishing AAAA records gives you direct connectivity without NAT at all.
Common Misconceptions
Opening a port on your router is not enough under CGNAT because the public address is not on your router. UPnP/NAT-PMP is not a backdoor into the ISP’s translator. Disabling your router firewall is counterproductive and risky. Changing DNS alone never fixes reachability; DNS only tells clients where to connect, it doesn’t create a path through NAT.
