IPv6 Prefix Delegation: How ISPs Assign and How You Configure
IPv6 prefix delegation gives you a block of globally routable space from your provider so you can number every LAN, lab, and DMZ without address collisions or NAT tricks.
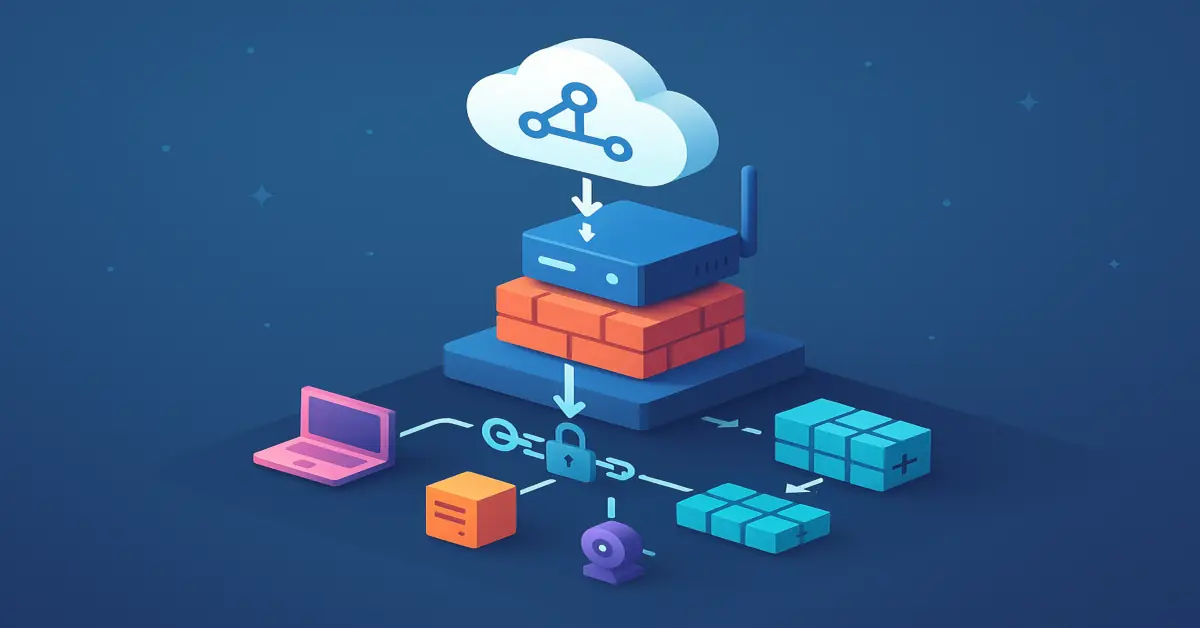
It works by having your edge router request a prefix using DHCPv6; the ISP delegates a larger block, your router slices that block into /64 subnets, and it advertises those subnets to hosts on each L2 segment using Router Advertisements (RAs).
Once you understand how the DHCPv6 lease timers, RA lifetimes, and routing fit together, you can make addressing stable, predictable, and easy to scale across VLANs—even if your provider gives you a dynamic prefix.
What IPv6 Prefix Delegation Actually Delivers
With prefix delegation, the ISP assigns a routed aggregate (commonly a /56, sometimes a /60, and for business service a /48) to your customer-premises equipment (CPE). The CPE doesn’t just pick a single address from that block; it subdivides the delegation into /64s, one per link. Hosts then form addresses via SLAAC or receive them from DHCPv6 on each LAN, while the CPE learns a default route on its WAN from upstream RAs and advertises a default route downstream to clients via RAs.
How ISPs Assign Prefixes
Most providers implement DHCPv6 Prefix Delegation (IA_PD). Your router identifies itself with a DHCP Unique Identifier (DUID). Many providers attempt to give you the same prefix when they see the same DUID again (“sticky” PD), but unless you buy a static allocation you should design assuming the prefix can change. Your router can include a size hint (for example, request /56), and some ISPs honor it. The lease comes with T1/T2 timers for renew/rebind plus valid and preferred lifetimes; if renewal fails, addresses eventually deprecate and then expire.
CPE Behavior and Standards
Baseline CPE behavior includes requesting a delegated prefix and numbering downstream links with /64s. On each LAN, the CPE sends RAs with the on-link /64, default route lifetime, and flags indicating whether hosts should use SLAAC only, SLAAC with DHCPv6 for other options (O flag), or DHCPv6 for addresses (M flag). Good CPEs persist their DUID across reboots to increase the chance of receiving the same prefix, and some implement the optional Prefix Exclude mechanism so a specific sub-prefix from the delegation isn’t used on a downstream link.
Designing Your Internal Subnets
Plan on exactly one /64 per L2 segment. Don’t carve smaller than /64 for production hosts; SLAAC, neighbor discovery, and many stacks assume /64. If you receive a /56, you have 256 distinct /64s—enough for generous per-VLAN segmentation. Name subnets clearly (for example, VLAN 10 “users”, VLAN 20 “voice”, VLAN 30 “iot”), and document which /64 maps to which VLAN.
Worked Example: Slicing a /56
Suppose the ISP delegates 2001:db8:1234:ab00::/56. You might allocate 2001:db8:1234:ab10::/64 to users, 2001:db8:1234:ab20::/64 to servers, 2001:db8:1234:ab30::/64 to iot, and keep the rest in reserve. If you prefer clean reverse DNS, consider grouping in nibble boundaries such as /60 chunks (each yields sixteen /64s) so ip6.arpa delegations are tidy.
Router and Firewall Configuration Steps
The exact CLI varies by platform, but the workflow is consistent. On the WAN interface, enable the DHCPv6 client and request IA_PD of your desired size (for example, /56). On each LAN SVI, assign a /64 derived from the delegated block and enable RAs. Tie those SVIs into your firewall policies. Ensure the router tracks PD renewals and updates routes and RAs when the prefix changes, and remember that default gateway discovery for the CPE and hosts is done via RA, not DHCPv6.
- Enable DHCPv6 client on the WAN and request IA_PD with a size hint.
- Persist the router’s DUID so the provider can “stick” the same prefix when possible.
- Derive a unique /64 per VLAN from the delegation and apply to each SVI.
- Enable Router Advertisements with appropriate M/O flags per VLAN policy.
- Allow essential IPv6 control traffic in the firewall (see below).
- Advertise DNS servers via RA (RDNSS) or via DHCPv6; advertise NTP only via DHCPv6 options.
- Monitor PD timers; renew before T1 and prepare for rebind at T2.
Must-Allow Control Traffic
Stateful firewalls should default-deny unsolicited inbound while allowing the control-plane that keeps IPv6 working. Permit DHCPv6 client traffic (UDP 546→547 and related replies), and allow ICMPv6 needed for neighbor discovery and path MTU: Router Solicitation/Advertisement, Neighbor Solicitation/Advertisement, Packet Too Big, Time Exceeded, and Destination Unreachable. On LANs, don’t block Neighbor Discovery or Multicast Listener Discovery; otherwise hosts won’t find routers or learn MTU, and large packets will black-hole.
Handling Prefix Changes Without Pain
Assume the prefix may change after a power cycle or when the ISP rehomes its edge. To survive gracefully, use RA lifetimes that let the router introduce “new” prefixes while deprecating “old” ones. Endpoints will prefer the new addresses but can still use the old ones briefly, which prevents abrupt session drops. Keep DHCPv6 address lifetimes short enough for quick convergence but not so short that you create churn. For internal-only services that must keep stable addresses, consider running unique local addresses (ULA) along with your global unicast and publishing both AAAA records where appropriate.
Sticky Delegation and PD Size Hints
Save the DUID in nonvolatile storage so the ISP can return the same block when possible. Configure a PD size hint that reflects your plan (for example, /56 for up to 256 VLANs). If the ISP provides less than requested, the router should gracefully adapt and number only as many VLANs as fit or use a deterministic mapping to a subset.
SLAAC, DHCPv6, and Address Stability
SLAAC lets hosts build addresses from the advertised /64 plus an interface identifier (IID). For stable host addressing without exposing MACs, enable stable IIDs as supported by modern OSs. If you need per-device reservations or option delivery (for example, NTP), run DHCPv6 either alongside SLAAC (O flag) or in managed mode (M flag). For client privacy, enable temporary addresses so browsers rotate source addresses while still keeping a stable IID for inbound reachability where needed.
DNS, Default Gateway, and Reverse DNS
Publish AAAA records for any service that must be reachable publicly. Remember that the default gateway is discovered via RA, not via DHCPv6. To deliver DNS resolvers to clients, use RA’s RDNSS option or DHCPv6; both are widely implemented. For reverse lookups, delegate the ip6.arpa zone that matches your nibble-aligned plan—/56 or /60 boundaries are easier to manage than a scattered set of /64s. Automate DNS updates from your router or orchestration when the prefix changes so records don’t go stale.
Security Posture in an IPv6-First Network
Drop unsolicited inbound by default and rely on stateful inspection rather than NAT. Keep ICMPv6 sufficiently open for PMTU and neighbor discovery. Segment aggressively using one /64 per VLAN, and apply least-privilege inter-VLAN policies. Log DHCPv6-PD events, RA changes, and drops of control messages; they are your early signals when renumbering happens or an upstream MTU changes.
Common Pitfalls and How to Avoid Them
Don’t split a /64 into /128s or /120s for hosts; you will break SLAAC and neighbor discovery. Don’t block essential ICMPv6 or you will break PMTU and see “works only for small payloads” tickets. Don’t forget reverse DNS; some services and anti-abuse systems use it as a signal. Resist NAT66; if you must abstract internal from external, use stateless NPTv6 with care, and treat it as an address-independence tool—not a security control.
Verification and Monitoring
On the CPE, verify an IA_PD was granted and that a default route was learned on the WAN. Check each SVI for a configured /64 and active RAs. On a client, confirm it has a global address in the expected prefix, can reach the router’s link-local, then an Internet v6 host, and that traceroute shows the expected path. Track PD renewals and rebinds in logs, and alert on RA changes so you know when the upstream renumbered you.
